File Systems
Samba
|
File Systems (alphabetical order) AFS CIFS CODA Ext2 GFS MS-DOS NFS NTFS Odyssey Samba Introduction What? How SMB Communication Security Future Links UNIX Some definitions and general technology |
A lot of emphasis has been placed on peaceful coexistence between Unix and Windows. The Usenix Association has even created an annual conference (LISA/NT--July 14-17, 1999) around this theme. Unfortunately, the two systems come from very different cultures and they have difficulty getting along without mediation. ...and that, of course, is Samba's job. Samba runs on Unix (and Linux) platforms, but speaks to Windows clients like a native. It allows a Unix system to move into a Windows "Network Neighborhood" without causing a stir. Windows users can happily access file and print services without knowing or caring that those services are being offered by a Unix host. Samba is an open source CIFS implementation (see also this site), and is available for free from the http://samba.org/ mirror sites.
Well, it provides that "interface" between Unix/Linux machines and Windows NT. This is achieved by 2 key programs (and several others): smbd (SMB deamon) and nmbd. Together they provide the main services of the CIFS: - File & Print services: the smbd is responsible for that. - Authentication and authorization: the smbd again, deviding between "share mode" and "user mode" (each user with own password) authentication and authorization. This is an important topic, as the Windows-way of authentication is unlike the linux/unix way, and Microsoft had their code protected. With v2, Samba introduced the first non-Microsoft-derived NT Domain authentication code. The eventual Samba goal is to completely mimic a Windows NT Domain Controller. - Name resolution: taken care of by the nmbd, involve the management of lists of NetBIOS names. Name resolution can be implemented via broadcasts, or the NBNS server (NetBIOS Name Service, commonly know as WINS) - Service announcement (aka browsing): also via the nmbd, involve the management and distribution of lists of NetBIOS names. This uses the LMB (Local Master Browser), its job is to keep a list of available services, and it is this list that appears when you click on the Windows "Network Neighbourhood" icon. The Domain Master browser coordinate browse lists across NT Domains, even on routed networks. Point for imporvement is the synchronization times (which can take up to an hour to get the correct list built). - Other commonly used utilities: 1. the smbclient, which is a simple SMB client with an interface similar to that of the FTP utility. It can be used from a Unix system to connect to a remote SMB share, transfer files, and send files to remote print shares (printers); 2. nmblookup, a NetBIOS name service client. Nmblookup can be used to find NetBIOS names on a network, lookup their IP addresses, and query a remote machine for the list of names the machine believes it ownes; 3. swat, an acronym for the Samba Web Administration Tool. Swat allows you to configure Samba remotely, using a web browser.
As the name already suggests, Samba uses SMB, the Server Message Block, is a protocol for sharing files, printers, serial ports, and communications abstractions such as named pipes and mail slots between computers. The Server Message Block SMB is a client-server request-response presentation layer protocol (REQ from client). The only exception to the request-response nature is when the client has requested opportunistic locks (oplocks) and the server subsequently has to break an already granted oplock because another client has requested a file open with a mode that is incompatible with the granted oplock. In this case, the server sends an unsolicited message to the client signalling the oplock break. Ok, the "normal operations". When you copy or move a file, the negotiated SMB size is different. The block size depends on a number of factors including:
From the specifications for Core versus Raw mode data transfers the following: the Windows NT redirector has the some requirements for performing raw mode I/O, all of which must be satisfied for raw mode I/O to occur. 1. The Server Message Block (SMB) protocol negotiated between the client and server must support Raw mode; 2. The server must be configured to support Raw mode; 3. The client redirector must be configured to allow Raw mode; 4. No other SMB requests are pending on the same Virtual Circuit (VC); 5. The I/O is not on a blocking named pipe; 6. For a READ request: the requested data size is equal to or greater than 2 times the currently configured request buffer size, and the read offset is not past the redirector's currently configured end-of-file; 7. For a WRITE request: the requested data size is equal to or greater than 1.5 times the currently configured request buffer size, and the write offset is not more than approximately 1 MB past the current end-of-file; 8. The I/O is to take no longer than 5 seconds to complete. The sole Core Mode Data Transfer requirement is the size of data blocks transferred. The default of 4Kb can be modified using the registry parameter HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \LanmanServer\Parameters on the remote server side. Network communication On the network it can use TCP/IP (NBT, specified in RFC1001 and RFC1002), NetBEUI or IPX/SPX as a communications protocol. (See Figure 1.)
The protocol elements (requests and responses) that clients and servers exchange are called SMBs. They have a specific format that is very similar for both requests and responses. Each consists of a fixed size header portion, followed by a variable sized parameter and data portion. There are four steps that the client and server must complete in order to establish a connection to a resource: establish a virtual connection - negotiate the protocol variant to speak - set session parameters - make a tree connection to a resource (read more if you like, I don't feel like copy-and-paste text too much). After connecting at the NetBIOS level, either via NBF, NetBT, etc, the client is ready to request services from the server. However, the client and server must first identify which protocol variant they each understand.
Dialects more recent than the Core and CorePlus protocols supply
information in the negprot response to indicate their capabilities
(max buffer size, canonical file names, etc).
The client sends a tcon or tconX SMB specifying the network name of the share that they wish to connect to, and if all is kosher, the server responds with a TID that the client will use in all future SMBs relating to that share.
Figure 2. SMB client-server session semantics. The component of Samba dealing with the security aspects, and more specific the differences in security between unix-like OSs and NT, is Winbind.Before Winbind, users had to be created ont he NT as well as the unix machine, with the according synchronization problems, overhead etc. The unified logon problem for Unix can be divided into three smaller problems to be solved: 1) obtaining NT user and group information 2) authenticating NT users and 3) password changing for NT users. Winbind unifies unix and nT account management by allowing a unix box to become a member of the NT domain. It asks the PDC to do the lookup on a low level via the NSS name resolution modules in hte C library. The implementation is as follows. Winbind runs as a deamon waiting for requests (client/server-model). These requests are generated by the NSS and PAM clients. - MSRPCs, Microsoft RPCs, are used to enumerate and authenticate domain users and groups and to obtain detailed infromation about individual users and groups (and may change their password). - NSS. The Name Service Switch is present in many unix(-like) systems and can resolve information like hostnames, mail aliasses etc. from different sources. - PAM is the abbreviation for Pluggable Authentication Module and important for defining the authentication and authorization. - User and group ID allocation. Winbind takes care of the conversion of RIDs to Unix ID numbers and vice versa. (RID is the relative identifier of a user or group created in NT). The results of all this mapping is stored persistemntly in a tdb database. - Result caching. To reduce the network cost of all the lookups, winbind uses a caching scheme based on the SAM sequence number supplied by NT domain controllers. If the sequence numbers don't mach, an update is requested from the PDC.
As it is Microsoft's intention to move from NT to Win2K, it will be necessary to make Samba compatible with the win2K. Some of those aspects of investigation are the following: CIFS Without NetBIOS: Microsoft will attempt to decouple CIFS and NetBIOS. NetBIOS won't go away, but it won't be required for CIFS networking either. Instead, the SMB protocol will be carried natively over TCP/IP. Name lookups occur via the DNS. Dynamic DNS: Microsoft will implement Dynamic DNS, which allows names to be added to a DNS server on-the-fly. Kerberos V: Kerberos V authentication + authorization is used with Win2k. See Windows 2000 Kerberos Authentication for more detail. Active Directory: The Active Directory appears to be at the heart of Windows 2000 networking. It is likely that legacy NetBIOS services will register their names in the Active Directory. Hierarchical NT Domains: Instead of isolated Domain Controllers, the Domain system in w Win2K network is hierarchical. The naming system is similar to that of the DNS. |
References and more information
Samba: An Introduction
SMB info
Microsoft KB article Q223140
Using Samba, Robert Eckstein, David Collier-Brown and Peter Kelly
Winbind, Unified logons between windows NT and Unix.
Doing the NIS/NT Samba
An Introduction to SMB/CIFS
 back to
back to 
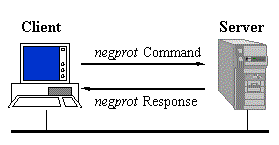 The client sends a negprot SMB to the server, listing the
protocol dialects that it understands. The server responds with
the index of the dialect that it wants to use, or 0xFFFF if none
of the dialects was acceptable.
The client sends a negprot SMB to the server, listing the
protocol dialects that it understands. The server responds with
the index of the dialect that it wants to use, or 0xFFFF if none
of the dialects was acceptable.
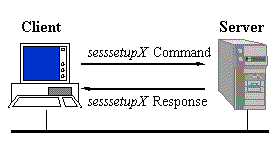 Once a protocol has been established. The client can proceed to
logon to the server, if required. They do this with a sesssetupX
SMB. The response indicates whether or not they have supplied
a valid username password pair and if so, can provide additional
information. One of the most important aspects of the response
is the UID of the logged on user. This UID must be submitted with
all subsequent SMBs on that connection to the server.
Once a protocol has been established. The client can proceed to
logon to the server, if required. They do this with a sesssetupX
SMB. The response indicates whether or not they have supplied
a valid username password pair and if so, can provide additional
information. One of the most important aspects of the response
is the UID of the logged on user. This UID must be submitted with
all subsequent SMBs on that connection to the server.
 Once the client has logged on (and in older protocols-Core and
CorePlus-you cannot logon), the client can proceed to connect
to a tree.
Once the client has logged on (and in older protocols-Core and
CorePlus-you cannot logon), the client can proceed to connect
to a tree.